Which of the following objects is NOT required to configure VPN-1/FireWall-1 for H.323 in this scenario?
Ann would like to deploy H.323 with a gatekeeper and gateway on her internal network. This
network is behind a VPN-1/FireWall-1 Enforcement Module. Which of the following objects is NOT
required to configure VPN-1/FireWall-1 for H.323 in this scenario?
which of the following statements are TRUE concerning SIP Services?
If you are using SIP or SIP_ANY, and the Source or Destination is Any, which of the following
statements are TRUE concerning SIP Services? (Choose two)
If the Service is:
Which of the following statements is TRUE?
Vered is a Security Administrator preparing to migrate her organization’s IKE VPNs from preshared secrets to PKI with certificates. Vered’s organization has client-to-site VPNs between
SecureClients and Enforcement Modules, and site-to-site VPNs between Enforcement Modules.
Vered will use the VPN-1/FireWall-1 Internal Certificate Authority (ICA), to generate and maintain
certificates. Which of the following statements is TRUE?
Vered can:
Which step in Mark’s installation plan is NOT necessary?
Mark is preparing to install VPN-1/FireWall-1 and has created the installation plan below.
1. Perform the following operations below in sequential order.
2. Install the operating system.
3. Configure routing and IP forwarding.
4. Configure name resolution.
5. Patch the operating system.
6. Set $FWDIR and $CPDIR environment variables.
7. Install VPN-1/FireWall-1.
8. Patch VPN-1/FireWall-1,
Which step in Mark’s installation plan is NOT necessary?
which type of key exchange?
Diffie-Hellman uses which type of key exchange?
If the Use Aggressive Mode check box in the IKE Properties dialogue box is enabled:
If the Use Aggressive Mode check box in the IKE Properties dialogue box is enabled:
What is the MOST likely cause of the problem?
Dr Billis setting up a new VPN-1/FireWall-1 Enforcement Module. The Rule Base is configured to
allow all traffic, and the Enforcement Module is set up as shown in the screen capture below. Dr
Billcannot get the new system to pass any traffic. What is the MOST likely cause of the problem?
System specifications:
Processor: 2.2 GHzRAM: 256 MBHard Disk: 10 GBOS: Windows 2000 Server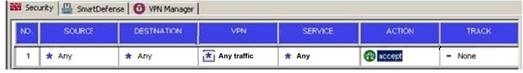
Results of ipconfig/all
View the following exhibit for the results of ipconfig/all.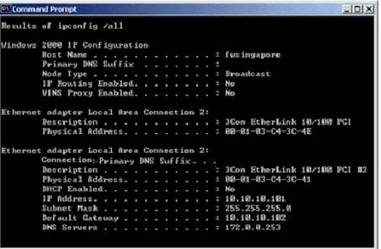
Which of the following encryption algorithms supports a key length from 128-bits to 256-bits and is outlined i
Which of the following encryption algorithms supports a key length from 128-bits to 256-bits and is
outlined in the new Federal Information Processing Standard publication?
Which of the following does NOT clear the password cache?
Static passwords such as VPN-1 & FirwWall-1 and operating system passwords are cached on
the desktop and users are not required to re-authenticate. Which of the following does NOT clear
the password cache?
Which of the following explanations addresses the auditor’s concerns?
Ann is a VPN-1/FireWall-1 Security Administrator. Her organization’s solution for remote-access
security is SecureClient. Ann’s organization is undergoing a security audit. The auditor is
concerned, because static passwords, such as VPN-1 & FireWall-1 and operating system
passwords are cached on the desktop, and users are not required to re-authenticate. Which of the
following explanations addresses the auditor’s concerns?

